Stolen Cargo in Container Terminals - Breaking the Chain
| Written by Constance Stickler
Container terminals play a central role in the global supply chain. 90% of world trade is carried out via shipping, which means that this 90% of world trade also stops at a container port at least twice on its journey. However, their significance also makes container terminals vulnerable to cargo theft. In this article, we look into what is stolen, why it is stolen and what is or can be done about it.

No video selected
Select a video type in the sidebar.
Supply chains must be efficient. And to be efficient, these supply chains require multiple stations and many moving parts to work together. Unfortunately, many of these stations are vulnerable to criminals; container terminals are no exception. In addition to the basic ones, new and more sophisticated security measures must be taken in order to keep pace with criminal developments.
Consequences of Stolen Cargo
Stolen cargo along supply chains is a billion-dollar business and causes a lot of work and reputational damage in addition to financial losses. The terminal must replace the monetary value of stolen goods, and insurance premiums can also increase following theft.
If negligence or inadequate safety measures are involved, this can result in legal consequences and insurance cancellations. This, in turn, may result in regulators stepping up their controls and becoming even more scrutinised in investigating security practices and compliance with relevant regulations.
Investigating thefts may disrupt container terminal operations. The potentially acute need to implement more effective security measures may come at a very inopportune time.
If the thefts repeat, the terminal's reputation will be damaged, and supply chain partners will lose trust. This can have severe consequences if customers switch to alternative terminals with better security.
The possible consequences make it clear: Regardless of whether the thefts are minor or significant, you want to avoid them. But what exactly is being stolen?
What Cargo Gets Stolen
Cargo thefts at container terminals target a wide range of goods. However, criminals usually target types of cargo that have a high value, are easy to transport and are in high demand on the black market:
- Electronics: Electronic devices such as smartphones, tablets, laptops, televisions and other consumer electronics have a relatively high value and are therefore often targeted.
- Pharmaceuticals: Medicines and other pharmaceutical products are in high demand for illegal distribution, especially if they require a prescription.
- Alcohol and Tobacco: Alcoholic beverages and tobacco products are a classic among frequently stolen goods. In many countries, for example, the price of cigarettes has risen enormously in recent years, making them an increasingly attractive object for theft.
- Clothing and Fashion Accessories: Designer clothing, luxury fashion items, and accessories are highly valued and easy to resell.
- Automotive Parts: Regarding vehicle parts, high-quality or unique rare parts are in high demand. They are sold on the black market or used to repair stolen vehicles.
- Building Materials: When it comes to building materials, high-quality or special building components are particularly lucrative.
- Metal and Scrap: Copper, aluminium, steel, and scrap metal are in high demand, as are metal goods or components.
- Jewellery and Precious Metals: Jewellery, gold and precious metals have a high market value and are attractive targets for theft due to their compact size.
- Art and Cultural Artifacts: Valuable works of art, cultural artefacts and antiques are often resold on the illegal art market.
- Food and Beverages: Non-perishable food and beverages are a popular target. Perishable goods, on the contrary, pose a logistical challenge in terms of their time-sensitive handling and are less in demand.
- Cosmetics and Beauty Products: High-quality cosmetics and beauty products are in-demand items for the black market. Here, too, products that require cooling are less attractive.
- Toys and Games: Popular and high-demand toys, video games and gaming consoles can be targeted, especially during peak shopping seasons such as Christmas.
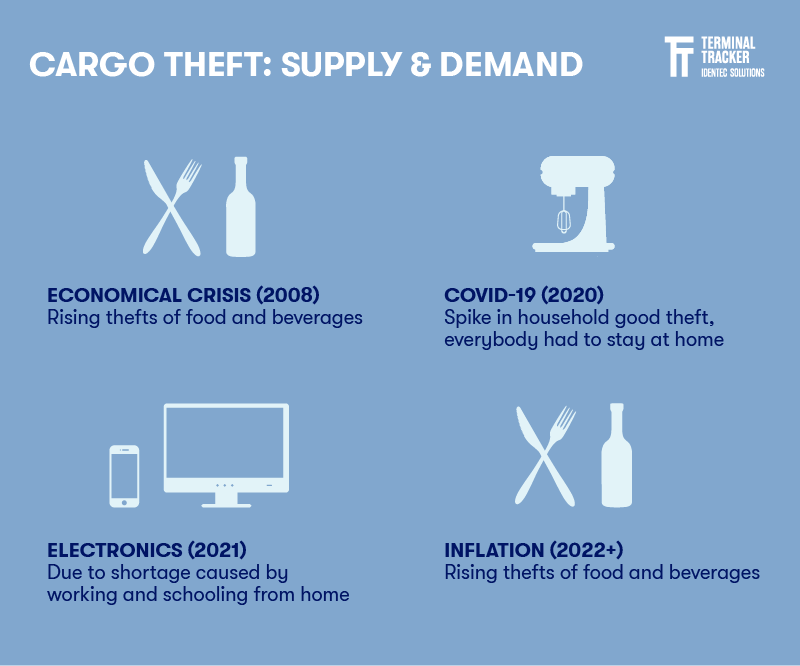
What is stolen is also directly related to the state of the global economy or global events. Scott Cornell, transportation lead and crime and theft specialist at insurance provider Travelers, points out in an interview with CNBC: "During the financial downturn in 2008, we saw a theft shift towards food and beverage where it stayed in that spot until the end of 2019. In 2020, we saw the target move to household goods, because we were all at home. In 2021, electronic theft was high due to some shortages as a result of all the working and schooling from home (1).
This list only includes those primarily stolen goods, and there is probably nothing that cannot be stolen should the opportunity or demand arise. Speaking of opportunity and demand: what circumstances may lead to theft?
Why Cargo Gets Stolen
"An open door may tempt a saint." Unfortunately, the door doesn't have to be wide open these days to tempt the proverbial saint. No matter how small, every loophole can become a target if there is a chance of loot.
At the most basic level, opportunity is the foundation of criminal behaviour; its principles were identified by Felson and Clarke (1998) as follows:
- Opportunity plays a role in causing all crimes.
- Crime opportunities are highly specific.
- Crime opportunities are concentrated in time and place.
- Crime opportunities depend on everyday movements.
- One crime produces opportunities for another.
- Some products offer more tempting crime opportunities.
- Social and technological changes produce new crime opportunities.
- Opportunities for crime can be reduced.
- Reducing opportunities does not usually displace crime.
- Focused opportunity reduction can produce wider declines in crime.
The bad news is that reducing opportunity doesn't eliminate crime in its entirety. The good news is that, with targeted measures, a significant reduction in crime can be achieved.
Now, let's take a closer look at the individual reasons that can lead to cargo theft at container terminals. It is essential to understand these motivations in order to develop effective security measures. The most common reasons include:
- Competitive Market: The competitive nature of the logistics industry, coupled with acute crises, can lead companies to focus solely on speed and cost efficiency. In such circumstances, security measures may be perceived as an additional, negligible cost; therefore, security protocol investments are not appropriately made.
- Insufficient security measurements: These include inadequate surveillance, inadequate fencing and barriers or gaps and breaches in the latter, poor lighting, spotty access controls, and weak enforcement of security protocols.
- Cybersecurity: Don't forget cybercrime. Cybercriminals may attempt to hack into terminal systems and manipulate data or security systems. This can include changing destination details, quantities, or other essential information to divert the cargo without detection.
- Poor Enforcement: The success of some security measures depends on their consistent adherence. If security protocols are poorly enforced or penalties for theft are not sufficiently deterrent, this can encourage wrongful acts.
- Personnel Issues: Due to the shortage of skilled workers, positions sometimes must be filled with "plan b" candidates or temporary staff. They often have not (yet) completed the appropriate training.
- Insider Involvement: In some cases, people with internal terminal information are involved in cargo theft. In addition to employees, these can also be contractors or people with temporary access to the port and work with external criminals.
- Organised Crime: Thefts are also orchestrated by organised groups that have appropriate resources and information. They may be interested in various activities, including smuggling and black market trading.
- Corruption: Corruption among law enforcement and customs officials can also contribute to criminal behaviour. Bribery and collusion with criminal entities can undermine security efforts by allowing stolen goods to pass through checkpoints undetected.
- High-Value Goods: Cargo thieves often target higher-value goods, such as electronics, pharmaceuticals, luxury items or other high-value consumer goods. Because of their higher resale value, these items are particularly attractive to criminals.
- Market Demand: Increased demand for certain goods can lead to their theft, leading perpetrators to particularly target shipments containing this cargo.
- Inadequate Tracking and Monitoring: When cargo is not tracked and monitored as required, it is easier for thieves to exploit loopholes in the system. Outdated tracking technologies lull some operators into a false sense of security.
What Can Be Done Against Stolen Cargo
Theft is an age-old problem, and people have tried to deal with it as long as it has existed. New technological developments offer new opportunities for criminals but also opportunities for greater security.
Some measures are mandatory, such as container seals, and then there are measures each terminal decides on its use, primarily technological and automated ones.
Elisa Rouhiainen, VP Sales Marine & Ports, suggests that interlocking advanced asset tracking technologies with real-time monitoring is paramount in safeguarding against container theft. It allows for proactive intervention and swift recovery in the event of unauthorised container movement.
When looking at protective measures against stolen cargo, let's start with the most apparent means attached to the container itself:
Container Seals
Container seals are an absolute must in international shipping. A container must be secured with at least one seal before a shipping company will allow shipping.
The seal cannot be opened without being irretrievably cut open. Usually, the container remains unopened, and the seal remains untouched until it is delivered to the buyer. The seals are usually made of metal or high-strength plastic, numbered and available in different designs, such as bolt seal, cable seal or barrier seal. After loading, they are fixed around the lock of the container.
There is no internationally uniform regulation for checking seal numbers at the container port. In the U.S., this is generally done when a container enters or leaves the port. The number is recorded at the gate and reported to the container line. It is then up to them to cross-check it against the documentation. In some other countries, the port authority only checks whether a seal is present and only sounds an alarm if it is faulty. At such ports, it is often customs that checks whether the correct seal is attached to the correct container.
If it is necessary to open the container in the event of an inspection, this must be done in a controlled and documented manner. Only authorised personnel such as customs officials, terminal operators or shipping company representatives are allowed to open the seal. The sealed condition is recorded beforehand: seal number, type and any visible markings, as well as the condition (intact or evidence of tampering). Specially suitable tools are used for opening to ensure that neither the container nor the cargo are damaged. After the inspection, a new seal is applied, and its number and other relevant information are documented for further shipping and further travel stops.
Internal and external staff
- Screening and Background Checks: Conduct thorough background checks on all personnel. In addition to our employees, this also includes temporary workers, contractors and service providers, as well as external drivers or warehouse employees. Anyone who has access to shipping information must be verified. This helps identify people with a history of criminal activity or links to organised crime.
- Access control: Restrict access and install access control measures to terminal areas where cargo susceptible to theft is stored. Only authorised personnel are allowed to enter these sensitive zones.
- Identification and Authentication: Provide all workers, including those with only temporary access, with badges that clearly identify roles and access permissions. Biometric authentication systems offer an even higher level of security against the use of stolen or forged credentials.
- Training and Awareness: Security training for all personnel is crucial to protecting against cargo theft. Emphasise the importance of cargo security and encourage employees to report suspicious activity. Confidential reporting mechanisms are needed so that security concerns can be reported without fear of reprisal.
- Valuable partnerships: Choose your business partners wisely and make sure they share your security philosophy. Also include external partners in training and new measures if possible. Collaboration and information sharing between terminal operators, shipping companies, law enforcement agencies and other stakeholders on potential security threats and known criminal activities, patterns and practices is particularly valuable.
- Audits and Assessments: Conduct regular security audits and risk assessments. This allows you to identify vulnerabilities in existing security protocols. If necessary, adapt the measures accordingly to counter new threats effectively.
Constructional measures against cargo theft
- Container Yard Layout: Plan the yard and the space for container piles to maximise visibility and avoid blind spots. Position and trim trees and shrubs so that they do not provide cover for criminal activity.
- Perimeter Fencing: Robust fencing prevents unauthorised access. Make sure all fences are designed to be difficult to climb.
- Access Gates and Checkpoints: Access gates and security checkpoints can be equipped with security guards to monitor the entry and exit of vehicles, cargo and personnel.
- Security Bollards: Security bollards can be used for strategic vehicle control and to prevent ramming attacks on access points.
- Dedicated Container Inspection Areas: Set up dedicated container inspection areas where efficient control is possible through appropriate technology and tools.
- Lighting Systems: Install adequate lighting throughout the terminal; this will improve visibility for surveillance cameras and on-site security personnel.
- Floodlights and Motion Sensors: Installing floodlights and motion sensors allows less visible areas to be made more visible at night.
Technical Solutions
- Real-Time Monitoring Solutions: Use Real Time Location System (RTLS) tracking technology to monitor every movement of containers, personnel and equipment within the terminal and have real-time location data available. In addition to individual container lift and drop events, handovers from one vehicle to another can also be monitored. If all these recordings are saved, every movement can be subsequently traced on a historical map. You will gain increased security by including external trucks in the monitoring. Mobile devices that are attached to the vehicle at the gate upon entry and removed again when leaving the premises are perfectly suitable for this purpose.
- Twist Lock Control: Solutions controlling the twist lock's opening ensure this only happens in the right places. This means that entire containers cannot simply be brought into hidden places and opened.
- Automated Container Weighing: If the containers are weighed automatically and the value is checked against the weight specified by the sender, an investigation can be initiated immediately if there are discrepancies.
- CHE Operator Access: Not only access to the site but also access and launching of Container Handling Equipment (CHE) itself are critical moments for preventing theft. This can prevent the terminal's own vehicles from being used for a criminal act.
- Shock Detection: Solutions that trigger an alarm in the event of (unreported) container damage can also help in the event of theft. When committing a crime, things usually have to happen quickly, and accidents tend to occur in the heat of the moment. Every crash triggers an alarm and is tracked, especially in unusual places or times.
- Security Cameras: Visible surveillance cameras can deter potential thieves and thus prevent crimes from occurring in the first place. In the event of theft, they provide valuable evidence for investigations and legal proceedings. The recorded videos can be used to identify people involved and to understand and provide evidence of the sequence of events. Their strategic placement enables the best possible visibility in areas that are otherwise difficult to see. To ensure effectiveness around the clock, night vision and low-light cameras can be used.
- Pan-tilt-zoom: Pan-tilt-zoom (PTZ) cameras can be panned and tilted remotely, and zooming makes it possible to focus on specific zones and activities. Advanced systems have built-in analytics and motion detection capabilities. This means unusual or suspicious activity can be automatically detected and an alert triggered.
- OCR: Using Optical Character Recognition (OCR) makes document forgery very difficult. Instead of manually entering an incorrect container number, you would have to hack into the automatically recorded data to manipulate it.
FAQs
Deception
- Impersonate a customer, driver of an external truck or port employee
- Changing delivery details, fraudulent delivery or release documentation
Fictitious pickup
A criminal poses as a driver or customer authorised to pick up the cargo. Either incorrect documentation is involved, or protocols to ensure personal identification and authorisation are not followed.
Inside job
Active participation of employees in the form of actions or knowledge transfer
Intrusion
- "Jump up": The door lock or door seal of a truck is broken, or the tilt curtain is slit (also possible in the presence of the driver).
- Break-in into the yard
Leakage Operations
Goods are stolen on a smaller scale over a more extended period of time. The aim is to ensure that it is not noticed that anything is missing for as long as possible.
Physical Tampering
The container is opened, and items are removed or replaced (e.g. with less valuable cargo). If one doesn't use suitable locks, it may take until the end of the shipping journey before the manipulation is noticed.
Technology-Based Tampering
The intervention occurs by hacking electronic systems in order to change databases or manipulate electronic documentation.
Takeaway
Container terminals, with their central position in the global supply chain, are vulnerable to cargo theft, a multi-billion dollar criminal industry. Among the consequences of stolen cargo are financial losses, enormous amounts of additional work and legal consequences. The main reason for theft is opportunity, in whatever form, physical or digital. The wealth of measures ranges from precautions on the containers themselves in the form of container seals to structural measures and the latest technology. It is also essential that all stakeholders involved work together to develop new, efficient measures to deter criminal activity, make it impossible, and, if an incident occurs, solve it quickly and, finally, to enable smooth container terminal yard operations.
Delve deeper into one of our core topics: Port Automation
Glossary
A background check is a process used by organisations to verify an individual's identity, history, and credentials. It typically includes examining criminal records, employment history, education, and other relevant information. Employers commonly use background checks during hiring to ensure candidates are qualified and trustworthy. These checks help mitigate risks, maintain workplace safety, and comply with legal requirements. The scope and depth of background checks can vary depending on the industry and position. (1)
A security bollard is a sturdy, vertical post designed to prevent unauthorised vehicle access and protect pedestrians and infrastructure from potential vehicle-related threats. These robust barriers are strategically installed in high-risk areas like government buildings, airports, and public spaces. Security bollards can be fixed or retractable, made from materials such as steel or concrete, and are engineered to withstand significant impact forces, effectively deterring vehicle-ramming incidents and enhancing overall site security. (2)
Sources:
(1) https://www.cnbc.com/2023/03/25/cargo-theft-led-by-food-and-beverage-is-surging-across-the-us.html
(2) https://thejusticecollaborative.com/types-of-background-checks/
(3) https://www.tymetal.com/blog/security-bollards-guide/#:~:text=Bollards%20are%20not%20only%20meant,vehicle%20access%20to%20prevent%20collisions.
Note: This article was updated on the 21st of January 2025

Author
Conny Stickler, Marketing Manager Logistics
Constance Stickler holds a master's degree in political science, German language and history. She spent most of her professional career as a project and marketing manager in different industries. Her passion is usability, and she's captivated by the potential of today's digital tools. They seem to unlock endless possibilities, each one more intriguing than the last. Constance writes about automation, sustainability and safety in maritime logistics.





